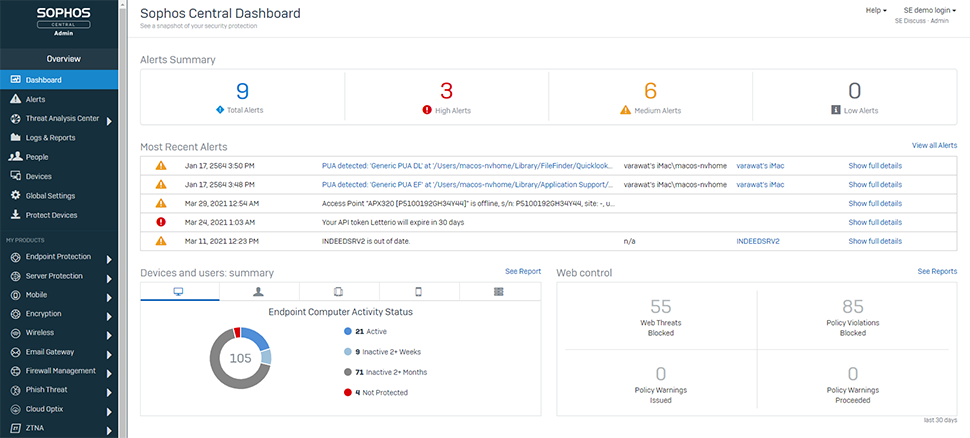
Sophos Intercept X Endpoint Advanced
Maintaining a Secure, Reliable Network Is Simple With the Right Support and SMB Networking Tools
Are you an SMB that doesn’t have an IT team? Or, maybe you have one, but they have too much on their plate? Then, you know keeping a network up and running and safe from intruders with limited internal resources can be a real chore. It’s easy to become overwhelmed and let networking issues keep you up at night. But there’s another option.
When you choose our SimplicITI managed services, our networking team becomes an extension of yours. With nearly 30 years’ experience matching businesses with the right technology and supporting them with the expertise to keep everything running smoothly, there isn’t much we haven’t seen or done. We are experts in many of the most popular SMB networking tools on the market today. Let us help you find the right mix of solutions, set them up and support you when issues arise.
Finally, you can get back to work, free from worry about when the next network issue might stop you in your tracks.
Sophos Intercept X Endpoint Advanced Key Features
Endpoint Detection and Response (EDR)
Detect and prioritize threats automatically.
Anti-Ransomware
Protect and automatically recover files plus employ behavioral analysis to stop future attacks.
Exploit Prevention
Block techniques used by attackers to seal credentials, distribute malware and leave undetected.
Deep Learning Technology
Artificial intelligence detects both unknown and known malware, without relying on signatures.
Central Management
Manage all your Sophos solutions from one unified dashboard.
Active Adversary Mitigations
Safeguard credentials, detect malicious traffic and prevent persistence on machines.
Synchronized Security
Sophos solutions automatically share data with one another and act accordingly.
Endpoint Detection and Response
Sophos Intercept X Endpoint Advanced with XDR combines powerful endpoint detection and response (EDR) with the industry’s top rated endpoint protection. Built both for threat hunting and IT security, EDR capabilities enable deep visibility into system activities, allowing you to detect and respond to advanced threats.
Intercept X Endpoint Advanced provides enhanced monitoring and investigation features to help identify the root causes of security incidents and respond effectively. Intercept X detects and investigates suspicious activity using artificial intelligence driven analysis. Unlike other similar tools, it replicates the skills of hard-to-find analysts, so you can add expertise without adding headcount.
Anti-Ransomware
To protect yourself from today’s ransomware attacks, which often include both real-time hacking and multiple advanced techniques, you need to protect the whole attack chain. Sophos Intercept X Endpoint Advanced does just that with deep learning that preemptively prevents attacks, and CryptoGuard, which rolls back any unauthorized encryption of data in seconds.
Exploit Prevention
Sophos Exploit Prevention is a powerful feature of Intercept X Endpoint Advanced that focuses on safeguarding your computer against software vulnerabilities that cybercriminals often exploit to gain unauthorized access. By proactively identifying and neutralizing the limited number of exploit techniques hackers use in file-less, malware-less attacks, Intercept X disrupts the attack chain, effectively stopping zero-day attacks in their tracks. This proactive approach thwarts hackers before they even have a chance to initiate their attacks, providing a robust layer of defense for your system.
Deep Learning Technology
Deep learning is used to enhance the accuracy and speed of malware detection. Deep learning algorithms are trained on large datasets of known malware samples, allowing them to recognize patterns and characteristics that are indicative of malicious code.
Here’s how Intercept X uses deep learning to predict and prevent attacks:
- Training Phase: During the training phase, the deep learning algorithms are exposed to a vast amount of malware samples. The algorithms analyze these samples, learning the distinguishing features that separate malicious code from legitimate software. This training process helps the algorithms build a robust understanding of malware behavior.
- Feature Extraction: Deep learning algorithms extract relevant features from files or processes to create a unique representation of each sample. These features capture intricate details, such as file structure, code sequences, and behavioral patterns.
- Detection and Analysis: When an unknown file or process is encountered on a protected system, Intercept X Endpoint Advanced utilizes the trained deep learning algorithms to assess its potential threat level. The algorithms compare the extracted features of the unknown entity with the learned patterns of known malware. If there is a high similarity, it indicates a potential malicious threat.
- Real-time Decision Making: Based on the analysis, Intercept X Endpoint Advanced makes real-time decisions on whether to block or allow the file or process. If the deep learning algorithms determine that it is likely to be malicious, the system takes immediate action to prevent any harm.
The utilization of deep learning technology in Intercept X Endpoint Advanced enhances its ability to detect both known and unknown malware threats. By continuously updating its knowledge through machine learning techniques, the system can adapt to new and evolving threats, providing robust protection against emerging attack vectors.
Central Management
Intercept X Endpoint Advanced offers a centralized management console that allows you to efficiently manage and monitor the security of all your endpoints from a single interface. This simplifies administrative tasks, such as deploying updates, configuring security policies, and generating reports.
Active Adversary Mitigations
Attackers are moving beyond malware to other techniques which allow them to move around in your systems and networks as a legitimate user, undetected. Intercept X Endpoint Advanced uses a variety of techniques, including concave utilization detection, APC protection and credential theft prevention to prevent hackers from hiding.
Synchronized Security
Sophos tools work in tandem with one another. For example, Sophos Firewall will coordinate with Intercept X Endpoint Advanced to identify, isolate and clean compromise devices. Once it neutralizes threats, it restores network connectivity with no human intervention.
Dive Deeper into Sophos Intercept X Endpoint Advanced
Learn more about what this robust security tool offers and explore licensing options.
Want to Learn More about Sophos Intercept X Endpoint Advanced?
As a leading managed service provider in Greensboro, Raleigh and beyond, who specializes in Sophos networking tools, we can help you design the network that will fit your needs today and for years to come. Or we can take some burden off your IT team and help support your existing network. Fill out the form to request more information.